- MSIX App Attach separates system, apps and data, enabling lightweight images and dynamic displays in Windows 11 and Azure Virtual Desktop.
- MSIX packages are converted into VHDX or CIM images with MSIXMGR and mounted using the Stage, Register, Deregister, and Destage phases.
- Visual Studio 2022, MSIX Packaging Tool, and App Attach Toolkit make it easy to create, sign, test, and publish modern packaged applications.
- Win32 isolation with AppContainer and other security technologies Windows They reinforce protection and reduce the attack surface.
MSIX App Attach has become the key component For those who want to isolate and deliver applications in a modern way on Windows 11 and in environments like Azure Virtual Desktop (AVD). If you've spent years struggling with giant images, App-V, MSI installers, or endless startup scripts, this way of working allows you to clearly separate the operating system, apps, and user data, and manage everything much more effectively.
In this article we will gather, organize and expand This course covers all the scattered information about MSIX, App Attach, Win32 application isolation, testing outside of AVDs, and best practices for packaging with Visual Studio and tools like the MSIX Packaging Tool or MSIXMGR. The goal is for you to leave with a comprehensive understanding: from what MSIX is, how to create packages, how to convert them to VHDX/CIM, how to test them locally, how to integrate them into Azure Virtual Desktop, and how all of this fits with application isolation and other Windows 11 security mechanisms.
What is MSIX and why is it so important for App Attach?
MSIX is Microsoft's modern packaging format For Windows applications, designed to gradually replace traditional .exe, .msi, App-V, ClickOnce, and similar formats. It's not just another installer: it combines traditional installation concepts with application virtualization and containers, resulting in clean, reliable, and easy-to-maintain packages for both on-premises and cloud environments.
The main advantages of MSIX are very focused on daily operationsIt offers a successful installation rate of around 99,96%, guarantees a clean uninstall, reduces bandwidth consumption by using 64 KB blocks, and prevents file duplication on disk between applications, allowing Windows to manage shared files without breaking app isolation.
For administrators, MSIX implies a change in mindsetYou no longer install the application "hard" into the system, but package it in an MSIX container, with a manifest (AppxManifest) that declares identities, Start menu entries, file associations, custom protocols, resource access capabilities, and other details of integration with the shell and the system.
Microsoft provides specific tools to facilitate this transition.: the MSIX Packaging Tool to convert existing installers (EXE, MSI, App-V, ClickOnce) to MSIX; the MSIX SDK to work with packages outside of Windows; App Installer to deploy packages from URLs or local media; and the Package Compatibility Platform to apply "fixes" when you don't have access to the source code.
MSIX App Attach: Delivering applications dynamically in Windows 11 and AVD
MSIX App Attach is the modern way to deliver MSIX packages App Attach dynamically deploys to physical and virtual machines, especially integrated with Azure Virtual Desktop and also supported on Windows 10/11 Enterprise. Unlike installing the app directly as a classic MSIX, App Attach is designed to mount the application from a disk image (VHD, VHDX, or CIM) and attach it to the system without it becoming a permanent part of the base image.
The great appeal of MSIX App Attach is the clear separation between system image, applications, and user data. The Windows image remains lightweight, applications reside in MSIX containers within virtual disks, and user profiles can reside in solutions like FSLogix, facilitating updates, rollbacks, testing, and reduced login times.
In AVD environments, MSIX App Attach eliminates the need Instead of having monolithic images with all possible apps, you upload the disks containing the MSIX packages to an Azure Files share, declare them as MSIX packages in the host pool, and assign them to application and user groups. The user sees the apps as if they were installed locally, but the system image remains clean.
Furthermore, MSIX App Attach is useful even outside of Azure Virtual Desktop.The APIs that support it are built into Windows 10/11 Enterprise and allow mounting, registering, and unmounting MSIX packages locally with PowerShellThis is ideal for testing scenarios, laboratories, or for validating the compatibility of a package before deploying it to production in an AVD.
Types of system images and why App Attach fits better into the modern model
When we talk about Windows desktop images or VDITraditionally, three approaches have been followed: department-specific “legacy” images, huge standard images with all applications, and, more recently, a modern approach where the base image is almost bare and the apps are delivered by streaming or dynamically attached.
In the legacy model, each user group has its own image (accounting, development, design, etc.). This simplifies the day-to-day work of each group somewhat, but at the cost of a maintenance, patching, and testing nightmare, because any change requires modifying several images and coordinating deployments.
The standard monolithic model reduces the number of images At the cost of bundling everything into a single image: all apps for all users in the same view, often combined with app masking techniques to hide applications depending on who logs in. Some management is gained, but the price is... high start times and a lot of complexity for updates.
The modern model favors a clean image with just the operating system, drivers and critical components, and leaves applications out, delivering them via MSIX, MSIX App Attach, or equivalent solutions. This model is a perfect fit for Azure Virtual Desktop and MSIX containers, as apps can be mounted and unmounted as needed.
From MSIX package to disk image: VHDX and CIM with MSIXMGR
To use an application with MSIX App Attach, the .msix extension is not enough.You need to convert that package into a disk image that can be mounted as a drive on the system. Microsoft allows three formats: VHD, VHDX, and CIM, although nowadays it's recommended to avoid VHD and prioritize VHDX or, even better, CIM (Composite Image File System) for performance and resource consumption.
The key tool for this process is MSIXMGRYou can download and extract it to a folder on a Windows 10 or 11 device with administrator privileges. With it, you can unpack an .msix file and create the corresponding .vhdx or .cim file ready for app attach using a console command.
The basic procedure for creating a CIM image It consists of opening a symbol of the system In an elevated location, navigate to the directory where MSIXMGR is located, ensure the destination folder exists, and execute a command like this:
msixmgr.exe -Unpack -packagePath "C:\msix\miapp.msix" -destination "C:\msix\miapp\miapp.cim" -applyACLs -create -fileType cim -rootDirectory apps
For a VHDX, the command is similar, changing the file type and the destination, which causes MSIXMGR to create and format the virtual disk, apply ACLs, and leave it ready to mount as a disk:
msixmgr.exe -Unpack -packagePath "C:\msix\miapp.msix" -destination "C:\msix\miapp.vhdx" -applyACLs -create -fileType vhdx -rootDirectory apps
Once the image has been generated, the next step will be to upload it. in a suitable shared resource (Azure Files for AVD or other sharing in on-premises environments) and prepare the scripts or configuration that will perform the mounting, registration and unmounting of the application according to the scenario.
Prepare the development environment: Visual Studio, App Attach Toolkit, and MSIX tools
If you are a developer and want to package your own apps for App AttachThe most convenient way to work is with Visual Studio 2022 and the Windows App SDK. For modern desktop projects with WinUI 3, the recommended template is “Blank App, Packaged (WinUI 3 in Desktop)”, which is already configured for MSIX.
First of all, it is advisable to have Visual Studio 2022 installedConfigured for C# or C++ depending on the project, and add the "Azure Development" workload from the Visual Studio installer. This facilitates direct publishing to Azure Virtual Desktop and other cloud integrations.
One very useful piece of equipment is the App Attach Toolkit extension.Available in the Visual Studio Marketplace. Once the extension is installed, you can create App Attach-ready MSIX packages directly from the IDE, generate the VHDX disk image, and, if desired, even publish the result to an AVD host pool without leaving Visual Studio.
For more traditional scenarios or for packaging existing Win32 appsThe MSIX Packaging Tool remains indispensable. It allows you to capture the installation process of an EXE or MSI file on a test machine (ideally using services like Windows Update or Windows Search stopped), configure the signing certificate, define first startup tasks, included services and other details, and finally produce a ready-to-use .msix.
Creating App Attach-ready packages from Visual Studio 2022
Once the App Attach extension is installed in Visual Studio 2022The typical workflow for a packaged WinUI 3 app is relatively straightforward. You start by opening Visual Studio in administrator mode (right-click, “Run as administrator”) to avoid permission issues when generating images and accessing certificates.
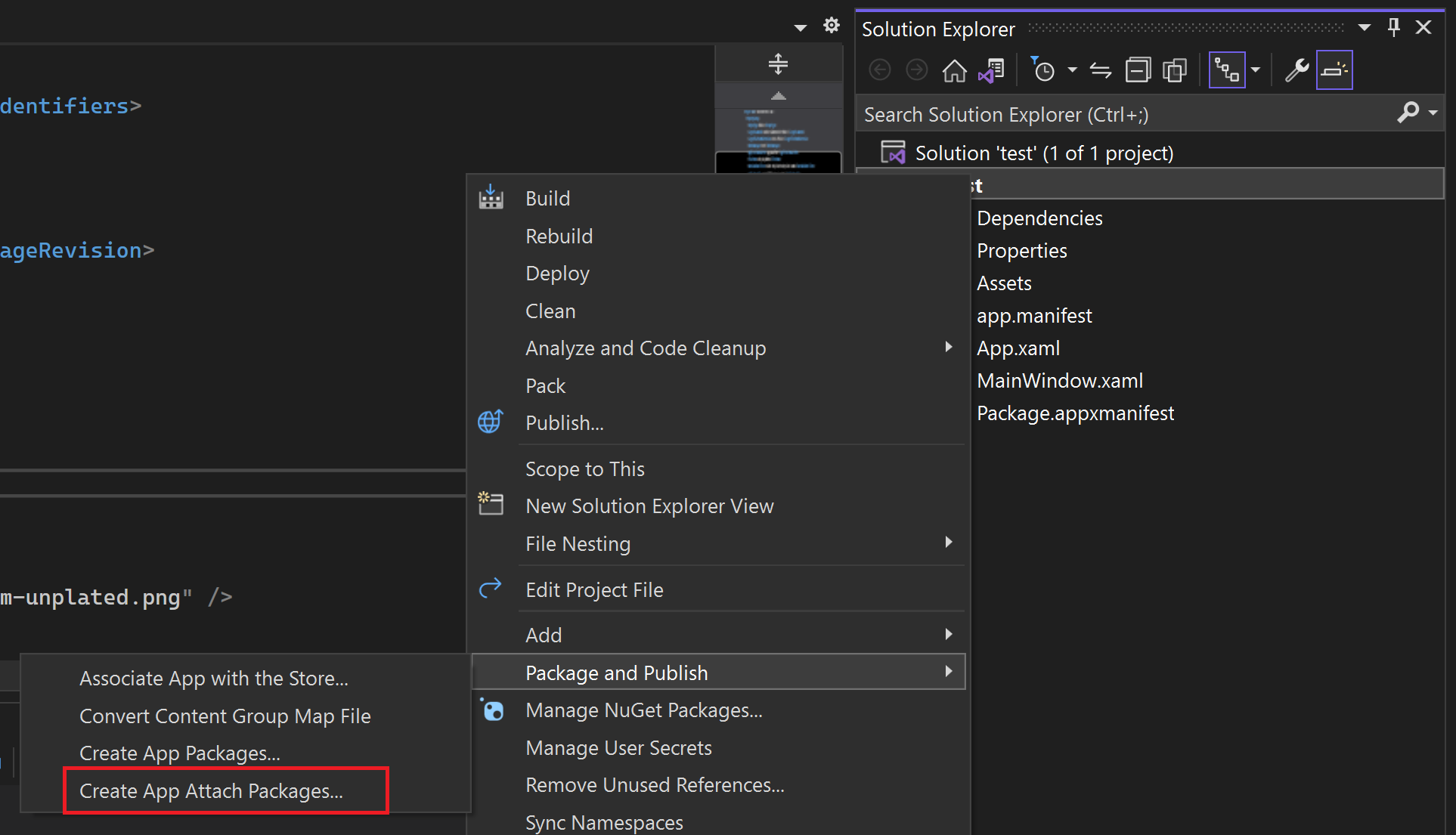
You create a packaged WinUI 3-type C# or C++ desktop project And, once your application is in a reasonable state, go to Solution Explorer, right-click on the packaged project, and choose "Package & Publish" > "Create App Attach Bundles." This option triggers the App Attach wizard.
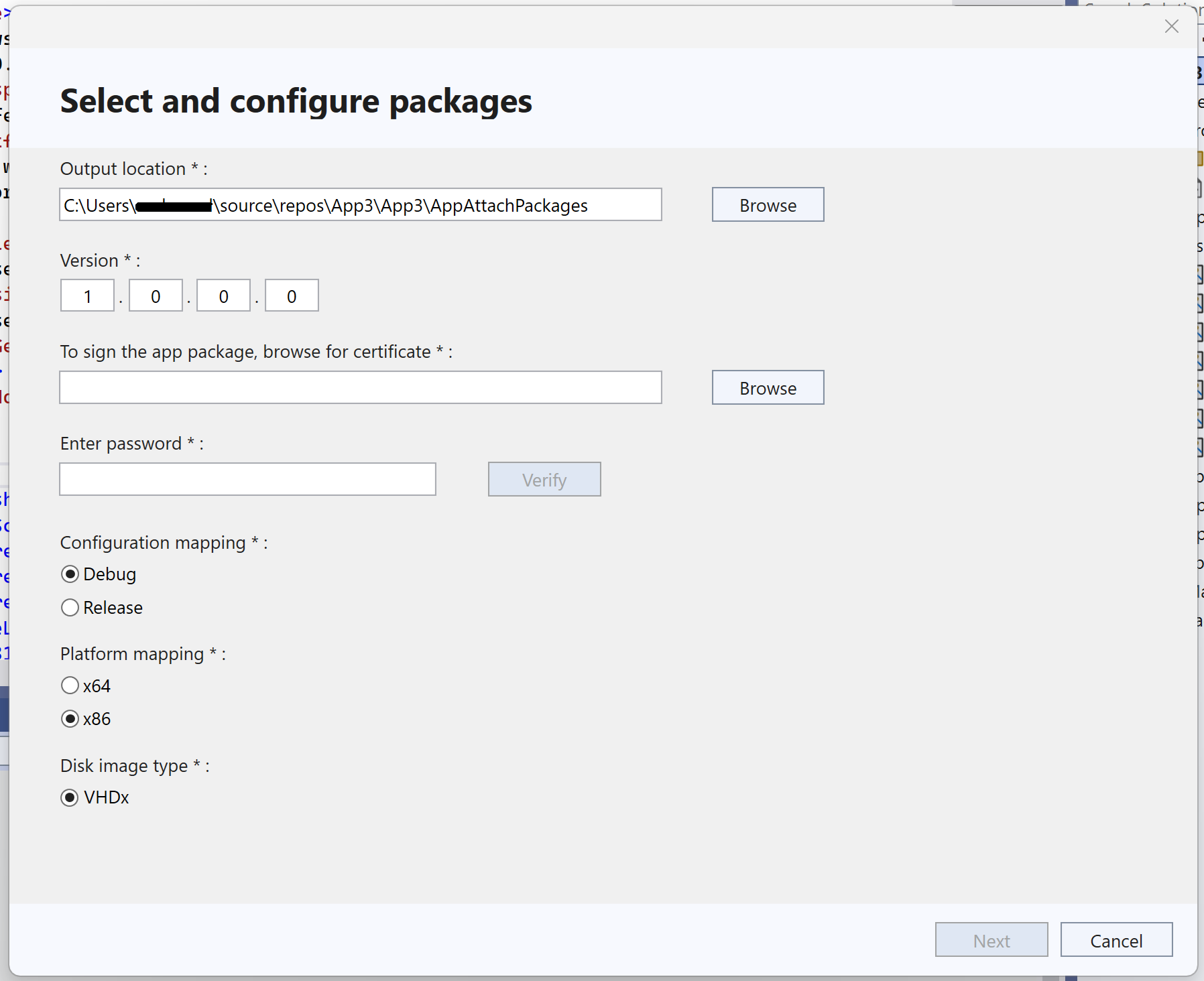
Within the wizard you can configure various aspects of the packageThe output location where the MSIX file and VHDX disk image will be generated, the target platform (x64, ARM64, etc.), and, most importantly, the certificate used to sign the package. You can select a certificate from the local store, use a .pfx file, or generate a new one on the fly.
The signature is a mandatory requirement for the package to be installed on other devices; that certificate must be trusted on the target machines (normally installed in Trusted Root or in Trusted People, as the case may be). In corporate environments it usually comes from an internal CA, while for public distribution it is common to use a commercial certificate.
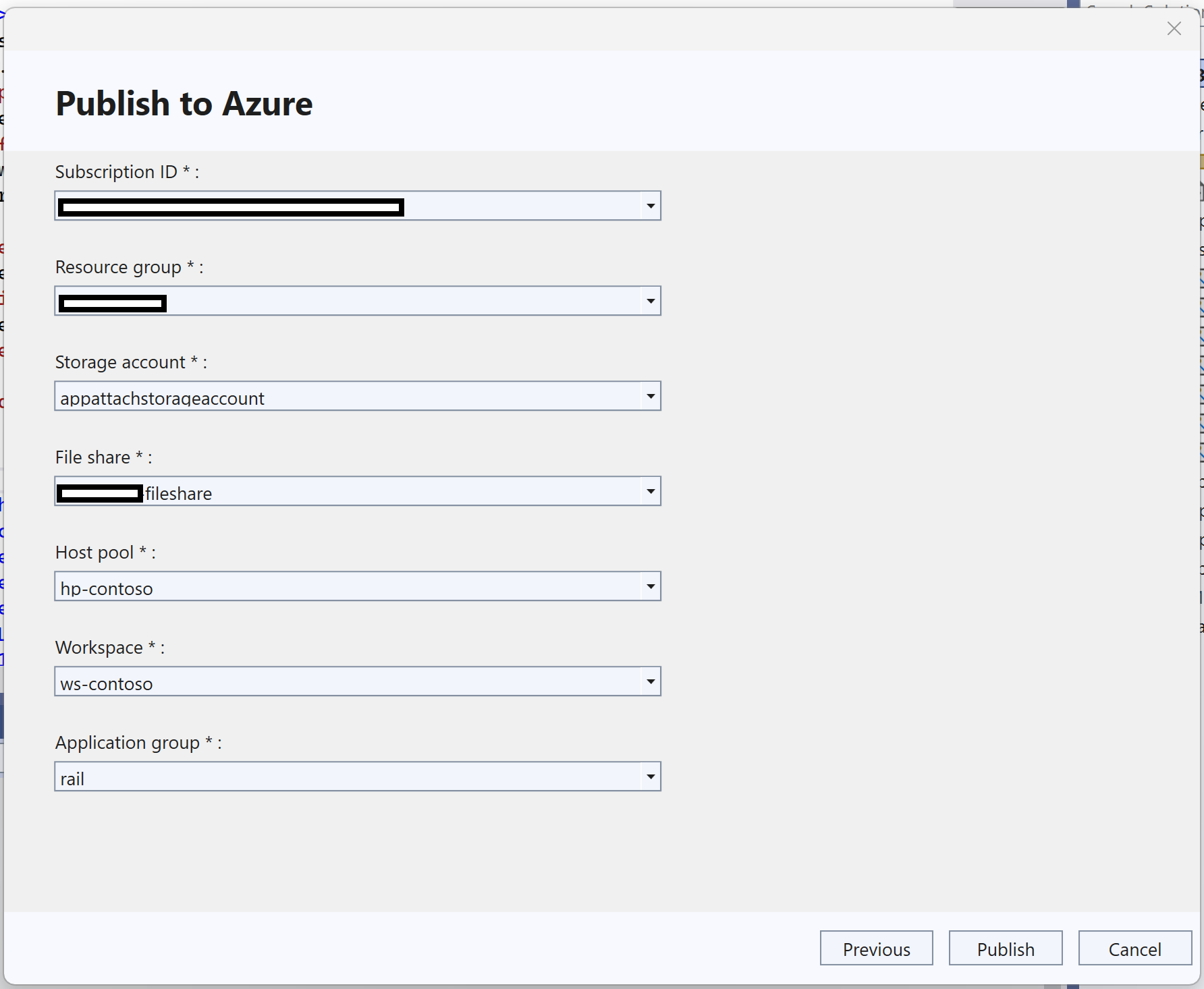
The extension also incorporates various exit options: simply create the disk image for manual distribution, perform a local link of the application on the development machine itself (very practical for testing), or publish directly to an Azure Virtual Desktop host group, specifying the subscription, resource group, and account. storageshared resource, application pool, workspace, and host pool.
Extension options: disk image, attach locally, or publish to AVD
The "Create only one disk image" option generates a VHDX or CIM It's ready for App Attach, but it doesn't publish or register it anywhere. It's ideal when you want to copy the disk to another share, manually upload it to Azure Files, or integrate it into another automation workflow that doesn't rely on the IDE.
The "Local Application Linking" functionality It creates the App Attach-ready package and publishes it to the local machine so you can test the real-world experience without needing an AVD host pool. The user can install the app, test its behavior, and then eject the disk and uninstall the package without leaving any significant traces.
The “Azure Application Partnership (AVD)” integration It allows for a complete transition to a production environment. The extension builds the MSIX package, generates the disk image, and uploads it to the AVD file share, registering the package in the corresponding application pool and linking it to the host pool and workspace so that users can see it.
In this Azure registration you must fill in several critical parametersThe Azure subscription, the resource group where the host pool resides, the storage account containing the file share, the share itself, the application pool, the associated workspace, and the host pool where the sessions will run are all required. With that information, a single click on "Publish" launches the entire automated process.
Internally, the extension minimally modifies the solution Adding an AppAttachPackages folder containing the MSIX and VHDX artifacts, and an appattach.config file with the metadata needed to replicate or maintain the configuration. While it can be safely ignored, versioning is recommended for traceability.
Prepare Azure Virtual Desktop and Azure Files for MSIX App Attach
In a real-world AVD deployment, MSIX App Attach relies on good design. storage and permissions. The usual practice is to use Azure Files integrated with Active Directory, and to organize permissions. NTFS and RBAC to properly isolate who can manage and who can only read the packets.
A typical scheme begins by creating two security groups In Active Directory: one for AVD users (e.g., AVDUsers) and another for session hosts (AVDSessionHosts). Users who will use the attached apps are added to the first group. Virtual machines Secondly, ensuring that all are synchronized with Azure AD via Azure AD Connect.
Then a storage administrator user is created (for example, StorageAdmin) which will assign permissions to the Azure Files share and manage NTFS. Once the Storage Account is created in Azure (ideally a Premium account for production, with the performance and redundancy you need), it is registered in Active Directory using the AZFilesHybrid module with PowerShell.
In terms of permissions, Azure RBAC is used to assign appropriate roles. such as “Storage File Data SMB Share Elevated Contributor” for administrators and “Storage File Data SMB Share Reader” for regular users and session hosts. In NTFS, the folder that will contain the packages (for example, \share\MSIXPackages) must grant at least read and folder listing permissions to the user and machine groups.
The last essential element is the signature certificates of the MSIX packages. You can use commercial certificates, a corporate PKI infrastructure, or self-signed certificates. For lab environments, it's quite common to use a Self-Signed Certificate created with PowerShell, export it as .pfx and .cer files, use the .pfx file in the packaging tool, and distribute the .cer file to all session hosts (via GPO, custom image, or manual installation) in the Trusted Root store.
Complete workflow for creating an MSIX package and its VHDX container
As a practical example, let's imagine we package 7-Zip. or another classic Win32 app. On a test machine joined to the domain and connected to the controller, we downloaded the app's .exe installer and the MSIX Packaging Tool from the Microsoft Store or its documentation page.
Within MSIX Packaging Tool we choose “Create application package”, option to create the package in this team As you proceed, the tool itself will check services like Windows Search and Windows Update, offering to disable them to avoid noise during the capture. Next, select the EXE installer and, if desired, specify arguments for a silent installation.
In the signing step, we select the .pfx certificate We have prepared the package, enter the password, and, if desired, a timestamp server. Next, we fill in the package information: internal name, display name, publisher, description, and version, trying to be consistent with the organization's naming convention.
The tool will launch the application installation.It's crucial here to disable any automatic updates for the app and, if necessary, restart your device before continuing with the wizard. This is a good time to open the application, verify that it works, and configure any initial setup you want to capture.
Upon completion, the initial startup tasks are defined. (entry points, paths to main .exe files), checks for associated services, and finally creates the .msix file and the conversion log. This package can then be installed on another Windows 10/11 system after importing the signing certificate.
To bring this MSIX to the world, App AttachThe next step is to create a disk container, typically a VHDX file, using Hyper-V and MSIXMGR or third-party utilities such as AppVentiX Community Tool or MSIX Hero. The result will be a .vhdx file that you can mount as a disk, partition, and forma tear, and on which to unpack MSIX with MSIXMGR to make it ready for dynamic mounting in host pools.
App Attach phases and testing outside of Azure Virtual Desktop
The App Attach engine always works in four distinct phasesStage (temporary storage), Register (user registration), Deregister (registration undoing), and Destage (mount removal). Stage and Destage are machine-level operations; Register and Deregister are user-level operations.
To test MSIX packages outside of AVD, you can follow this same scheme On a Windows 10/11 Enterprise machine using PowerShell, first mount the disk image (VHDX/CIM) with the appropriate command, obtain the volume's deviceId, locate the AppxManifest.xml, construct the path, and use the Windows.Management.Deployment.PackageManager APIs to run StagePackageAsync with the StageInPlace option.
Once the package is in a “staged” stateYou register it for the user by calling Add-AppxPackage and pointing to the AppxManifest file within Program Files\WindowsApps. At that point, the application appears in the session like any other installed app, and you can open it to verify its functionality and performance.
When you finish testing, unregister with Remove-AppxPackage using the fully qualified package name (msixPackageFullName). Then proceed to destage: unmount the disk image with the command corresponding to the format (VHDX, VHD, CIM) and, if you want to be thorough, repeat Remove-AppxPackage -AllUsers to ensure that it is not registered for anyone.
This same pattern of Stage/Register/Deregister/Destage It can be automated using startup, logout, and shutdown scripts with group policies. This way, without needing a control plane like AVD, you could simulate App Attach behavior on physical machines or controlled environments.
Win32 application isolation, AppContainer, and security in Windows 11
MSIX and App Attach are not isolated entities; they are part of a larger strategy. System hardening in Windows 11, where Win32 application isolation, UWP application containers, Windows Sandbox, WSL, and virtualization-based enclaves play a key role.
Win32 application isolation is supported by AppContainer To run processes with low integrity levels, strictly limiting accessible APIs and resources. First, the app is launched within this hard-constrained container; second, it is granted only the necessary capabilities through the MSIX package manifest, which acts as an access contract for Windows securable objects.
To help developers fine-tune these capabilities To avoid going in blind, there's Application Capability Profiler (ACP), which allows you to run the app in learning mode. In this mode, if a capability is missing, instead of blocking access, it's temporarily enabled, and the app records what capability would be needed when it runs in true isolated mode.
Beyond Win32 isolation, UWP apps and other experiences They run in application containers that also operate at a low level of integrity, restricting access to the file system, registry, and network (for example, limiting access to localhost). This drastically reduces the attack surface if an app is compromised.
Complementing this approach are Windows Sandbox (Windows Sandbox) to run untrusted Win32 applications in disposable environments, WSL with controls such as Hyper-V firewallDNS tunneling and automatic proxy managed by tools like Intune, and virtualization-based security enclaves (VBS) that act as software TEEs to protect secrets even against highly privileged attackers.
Integrated application management, wsappx and advanced scenarios in AVD
In Windows 11 multi-session environments in AVDs, another curious issue arises.: the management of integrated applications (Calculator, To Do, Paint, Notepad, etc.) and the impact of the wsappx process on the CPU, especially when many users share a host.
Many administrators want to disable the Microsoft Store. via GPO to reduce resource consumption and block unauthorized installations. The problem is that, when it's disabled, pre-installed AppX apps stop updating via the standard method, and not all of them are available in Winget, which is usually the preferred tool for automated deployments.
Possible strategies involve combining several techniquesOptions range from leaving the Store active for administrative purposes only and controlling its use with strict policies, to migrating certain integrated apps to packaged versions like MSIX and even App Attach when feasible. In some cases, integrated applications can be replaced with manageable equivalents using Winget or a custom MSIX.
Regarding wsappx, optimizations can be made. de Bootminimize background tasks related to the Store and AppX, and measure DPC latency to detect which specific operations are generating load. In any case, moving as many applications as possible to the MSIX + App Attach model helps to better control each app's footprint on the system.
Passionate writer about the world of bytes and technology in general. I love sharing my knowledge through writing, and that's what I'll do on this blog, show you all the most interesting things about gadgets, software, hardware, tech trends, and more. My goal is to help you navigate the digital world in a simple and entertaining way.
