- Check policies (GPO), services, and RDP listener before touching the firewall to isolate the source of the blocking.
- Check port 3389, active rules and certificates; a conflict or broken certificate prevents the listener from listening.
- Authentication errors (CredSSP, NLA, permissions) are as common as network errors; align it with updates and groups.
- If you cannot open ports, use an RDP gateway with MFA or a secure broker that avoids exposing port 3389.

If your Remote Desktop connection suddenly stops working, you might think it's the firewall or that the machine is turned off. But with RDP, the real culprit is often... network policies, GPOs, or services that block port 3389 Without warning. The good news: with an ordered sequence of checks, you can isolate the fault in minutes.
In this guide you will find practical and proven procedures for diagnosing and correcting policies, rules, and configurations that prevent RDP in Windows, both on local and remote equipment, on a corporate network, VPN and even in clouds like Google Cloud. You'll also see how to deal with authentication errors (CredSSP), certificates, port conflicts, DNS and performance, plus alternatives when you need something that works without opening ports.
How to detect if a policy or network is blocking RDP
Before touching the registry or the firewall, it's a good idea to confirm if the problem is with network reach, filtering, or saturationA useful shortcut from another computer is to test for port access using utilities like psping: psping -accepteula <IP-equipo>:3389. If you see Connecting to … with attempts that don't come to fruition, or a The remote computer refused the network connection, indicates an intermediate block or service outage.
Test from multiple sources (another subnet, another VPN, home network, or 4G) to see if the blocking is selective by segment or by originIf it fails from all sides, it's probably being blocked by a perimeter firewall or Windows itself. If it only fails from one side, check the allowlists. ACLs and firewall rules intermediate.
Quickly check the status of RDP and its services
Start by verifying that the remote system allows Remote Desktop connections and that the services are running; this rules out the basics with two or three commands.
On a local machine, enabling RDP is as simple as opening Settings and activating it. Remote Desktop ( using Windows 11 Remote DesktopFor finer control (or if the UI is unresponsive), check the log at: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server y HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services. The value fDenyTSConnections must be 0 (value 1 means RDP disabled).
Remotely, connect to the network registry from the Registry Editor (File > Connect to Network Registry), navigate to the same paths, and confirm that there is no policy forcing the blocking; if it appears fDenyTSConnections=1, change it to 0 and take note of whether It returns to 1 after a few minutes. (sign of prevalent GPO).
Also check that the necessary services are running at both ends: Remote Desktop Services (TermService) y Remote Desktop Services UserMode Port Redirector (UmRdpService)You can do it in services.msc or with PowerShellIf you need guides for editing services, consult Modify services in Windows 11If anyone is detained, Start it and try again.
Group Policy Object (GPO): How to block and how to unblock
When RDP cannot be activated through the interface, or the registry value is reverted, it is almost certainly being enforced by a policy. To identify this policy on the affected machine, run the following command on a CMD high gpresult /H c:\gpresult.html and opens the report; under Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Connections the directive is looking for Allow users to connect remotely using Remote Desktop Services.
If you see it as DisabledConsult the report to find out what the GPO that prevails and in what scope it applies (site, domain, or OU). Also review how Joining a domain in Windows If you suspect domain problems, from the Group Policy Object Editor (GPE) at the appropriate level, change that policy to Enabled or Not Configuredand in the teams involved, it forces the application with gpupdate /force.
If you manage via GPMC, you can also remove the link from that GPO in the organizational unit where it applies to the affected equipment. Remember that if the block came from SOFTWARE\PoliciesThe GPO will rewrite the registry until you delete or edit the policy.
For a remote machine, generate the report the same as on a local machine, adding the computer parameter: gpresult /S <nombre-equipo> /H c:\gpresult-<nombre-equipo>.htmlwhich will give you the same data structure to investigate the causative GPO.
Listener, port and conflicts on 3389
Even with the directive correct, if the RDP listener isn't listening, there won't be a session. In elevated PowerShell (local or remote with Enter-PSSession -ComputerName <equipo>), executes qwinsta and verify that the entry exists rdp-tcp with state ListsIf it does not appear, the listener may be damaged.
A reliable method involves exporting the listener key from a healthy machine with the same version of Windows: HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-TcpOn the affected computer, save a copy of the current state with reg export "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-tcp" C:\Rdp-tcp-backup.reg, removes the key (Remove-Item -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-tcp' -Recurse -Force), the good .reg file matters and restarts TermService.
After that, check the port. RDP should be listening on 3389. Check out HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\<listener> and value PortNumberIf it is not 3389 and you do not have a security reason to change it, revert to 3389 and restart the service.
To detect conflicts, run cmd /c 'netstat -ano | find "3389"' and note the PID that is in state LISTENINGThen, with cmd /c 'tasklist /svc | find "<PID>"' Identify the process. If it is not TermServiceReconfigure that service to another port, uninstall it if it's unnecessary, or as a last resort, change the RDP port and connect by specifying IP:port (not ideal for standard administration).
RDP certificates and MachineKeys permissions
Another common cause of incomplete connections is a broken or unrecreated RDP certificateOpen the certificate MMC for the team account, go to Remote Desktop > Certificates and remove the self-signed RDP certificate. Restart the Remote Desktop service and refresh: a new one should be created automatically.
If it doesn't appear, check the permissions of C:\ProgramData\Microsoft\Crypto\RSA\MachineKeys. Make sure that BUILTIN\Administrators have total control and Everyone count on Reading and writingWithout these ACLs, Windows cannot generate the key and certificate required for RDP.
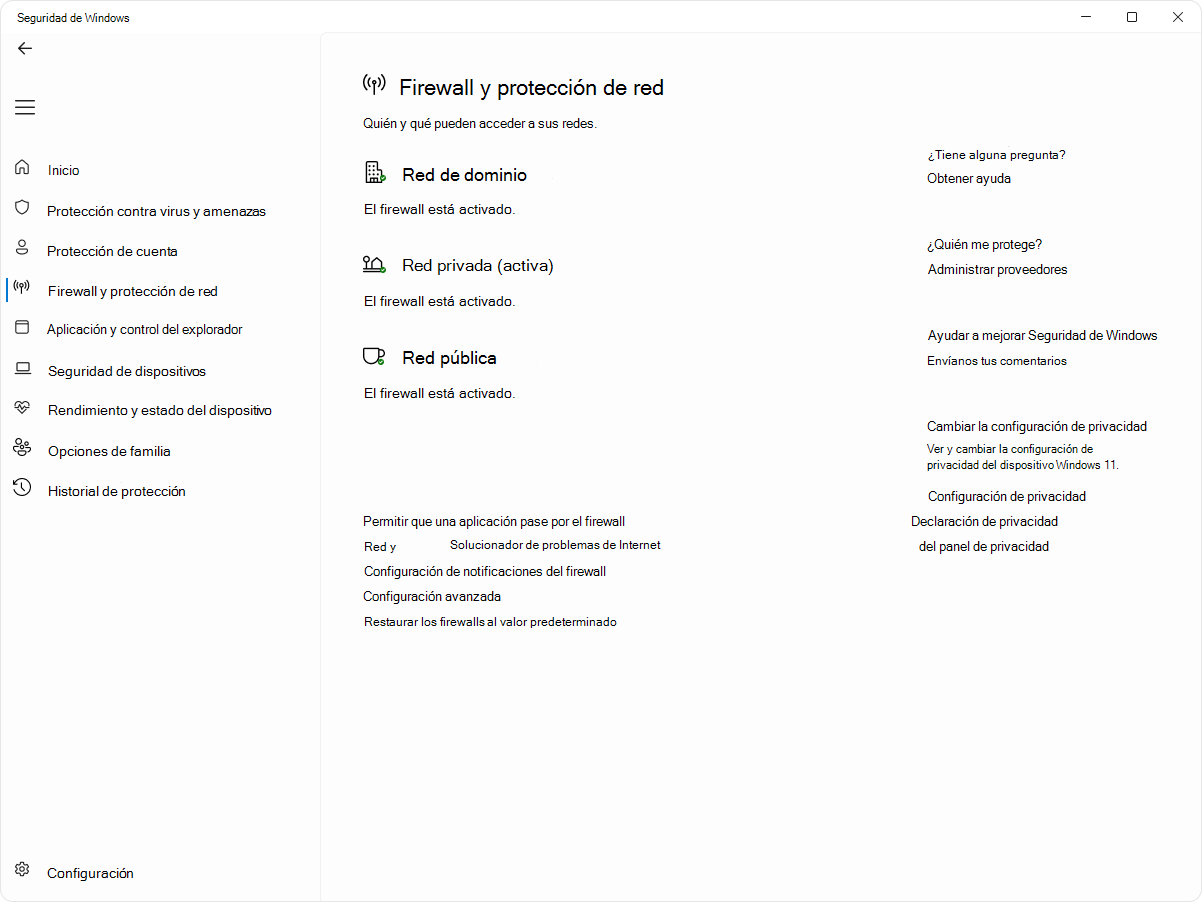
Windows Firewall and range testing
On client and server systems, Windows Defender The firewall needs open inbound rules for RDP. Check the built-in rule “Remote Desktop – User Mode (TCP-In)"With netsh advfirewall firewall show rule name="Remote Desktop - User Mode (TCP-In)"; must be Enabled, applied to appropriate Profiles, TCP Protocol and Local Port 3389.
If you manage via interface, go to Windows Defender Firewall > Allow an app or feature and select “Remote Desktop” in Private (and in Public only if you have a clear justification). In “Advanced Settings”, verify that the inbound rule for TCP 3389 is active. As a troubleshooting step (not on public networks), you can temporarily disable the firewall to check if the connection goes through and then immediately re-enable it.
From outside, the clearest way to verify arrival at the port is psping: psping -accepteula <IP>:3389If you get 0% lossThe network stack and firewall allow the connection. If everything is 100% loss o refusedIt's time to escalate to an intermediate network/firewall or review NAT, VPN and filters between segments.
Authentication: credentials, CredSSP and permissions
Type errorsYour credentials didn't work" or "The account is not authorized for remote login"They are usually trivial to fix: check username/password is correctly formatted (for example, DOMINIO\usuario), deletes any outdated credentials in the Credential manager and confirm that the account is not blocked.
With CredSSP, if the equipment isn't up to date, a difficult-to-interpret authentication failure will occur. Make sure you have Windows updated on both client and host. As a shortcut in older environments, you can enable in GPO “Allow delegation of saved credentials with NTLM-only server authentication” or, via the registry, set AllowEncryptionOracle a 2 en HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System.
Don't forget group membership: on non-domain teams, add the account to Remote Desktop Users From Computer Management > Local Users and Groups. In the domain, validate that membership complies with the Active Directory policy in effect before touching anything.
DNS, VPN, and other network variables
If you connect by name and the host's IP address has changed, the client may still be pointing to an old address due to caching. Clean up with ipconfig /flushdns and, if it persists, use the Direct IP To rule out a resolution problem, check that the adapter uses the correct DNS server in Control Panel > Network Center > Change adapter settings.
With VPNs, some providers block or redirect port 3389, or encapsulate it in a way that conflicts with RDP encryption. Disconnect the VPN and test, or adjust the policy to allow RDP. split tunneling or “allow apps”. If you detect interruptions or black screens, lower the MTU by one point: netsh interface ipv4 show subinterfaces to see it and netsh interface ipv4 set subinterface "Ethernet" mtu=1458 store=persistent to adjust it.
If the client seems unresponsive but the session is still there, it could be an issue with resolution or window sizeIn the Remote Desktop Connection client (mstsc), click "Show Options" and on the Display tab move the resolution slider or enable full screen; many "connections that aren't working" are fixed. adjusting the window.
Known issues and cloud services: Windows 11 24H2 and Google Cloud
Cases have been reported where connecting via RDP to Windows 11 24:2 The session freezes on startup, especially in Virtual machines Regarding the hypervisor. Some interim patches haven't resolved it; keep your system fully updated and test the hypervisor's video/vGPU drivers, as sometimes the problem lies with the hypervisor. RDP chart or stackRestarting the host temporarily restores connectivity, but the solution involves cumulative updates and drivers/firmware.
In Google Compute Engine, in addition to the local Windows password (reset it from gcloud or the console), check the rule default-allow-rdpList of rules with gcloud compute firewall-rules list and, if it's missing, create one with gcloud compute firewall-rules create allow-rdp --allow tcp:3389. Verify that you are using the Correct external IP address to gcloud compute instances listIf the OS is misconfigured, access it via interactive serial console and runs:
• Service: net start | find "Remote Desktop Services" (if it's not there, net start "Remote Desktop Services")
• Enable RDP: reg query "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections (0 is OK; if 1: reg add ... /d 0)
• Firewall: netsh advfirewall firewall show rule name="Remote Desktop - User Mode (TCP-In)" (but, netsh firewall set service remotedesktop enable)
• Security layer: reg add "HKLM\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /v SecurityLayer /t REG_DWORD /d 1 /f
• Default NLA: reg add ... /v UserAuthentication /t REG_DWORD /d 0 /f
Advanced diagnostics: events, network and tools
When the above does not clear up the problem, it's time to look events and tracesOpen Event Viewer and check in Windows Logs > Application and System, and in the sources TerminalServices-RemoteConnectionManager y Microsoft-Windows-RemoteDesktopServices-RdpCoreTS for clear errors in each attempt.
On a network, capture with Wireshark and filter by tcp.port==3389 Check for SYN/SYN-ACK signals, resets, or mid-connection drops. If there's no traffic, the block is en route; if there is traffic and it drops during security negotiation, suspect... encryption mismatch/NLAAs a quick test of port openness, telnet <IP> 3389 (If it connects, the port is accessible.) You can also use other utilities such as using ntttcp in Windows for performance and saturation testing.
Microsoft offers an RDP Protocol Monitor/Analyzer, and in Windows Server 2012/2012 R2, the Remote Desktop Services Diagnostic Tool To identify bottlenecks. If you can't dedicate time to each recurring issue, prepare scripts: netsh int ip reset && netsh winsock reset for network, and taskkill /F /IM mstsc.exe && net stop termservice && net start termservice to clear RDP sessions and restart services (warning: shorten active sessions).
The infamous “RDP – An internal error has occurred”

This generic message often hides a safety misalignment between client and server. Check that the encryption level and security layer match (in GPO: Session Host Security > “Require the use of a specific security layer” and select RDP (if TLS fails). If the server requires NLA and the client cannot, temporarily uncheck NLA in System Properties > Remote to check if this is the cause.
Other factors: outdated RDP clients versus newer servers, domain trust issues (Rejoining the domain sometimes resolves this), or security profiles that enforce encryption that the other end doesn't support. In Customer Experience, enable automatic reconnection and persistent bitmap cache for more resilient sessions.
When the error appeared after a Windows update and none of the above makes sense, consider reverting that specific patch (Panel > Windows Update > History > Uninstall updates), after consulting technical forums (for example, threads of Patch Tuesday) in case it's a known problem.
Performance, capacity and multimedia
If the complaint isn't "it won't connect" but "it's choppy," start by reducing the load from the RDP client: down resolution and color depthDisable background, visual styles, and font smoothing in the Experience tab. These measures reduce bandwidth consumption and improve latency.
On the server, check CPU/RAM/Disk in the Task ManagerIf it's at its limit, any RDP session will fail. Remember that Windows Desktop only allows a simultaneous sessionWindows Server has two default administrative licenses and requires additional RDS CAL licenses.
For audio, configure the RDP client > Local Resources > Remote Audio to “Play on this computer”, and verify that the services Windows Audio and “Windows Audio Endpoint Generator” are running. For heavy video, RDP isn't always ideal; some older environments mention RemoteFX, but today it's better to opt for Adaptive codec and modern acceleration or evaluate tools designed to streaming graphic.
Quick cases and express solutions
If Windows Defender is blocking the connection in Windows 10/11, go to Windows Defender Firewall > Allow an application and activate “Remote Desktop” by checking the Private boxes (and Public only if applicable), press Accept and test. In many real-world incidents, these three clicks They have been the difference between frustration and success.
If you need to change the port because another service is using 3389, edit HKLM\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp > PortNumberFor example, put 3390, restart the service and connect as IP:3390Remember to adjust firewall and NAT to that new port.
Alternatives and gateways when you can't open ports
In networks where opening 3389 is impractical (or you don't want to expose it), consider solutions with cloud mediator that avoid manual rules and DNS hassles: RealVNC Connect offers SSO and centralized management; Chrome Remote Desktop It's free and easy if you already use Chrome; TeamViewer and AnyDesk They prioritize ease of use and cross-platform speed. There are also suites such as TSplus, aimed at strengthening security and simplifying remote access at scale.
If you're going to stay in RDP, the safe option is to set up a Remote Desktop Gateway (RD Gateway)Require NLA and MFA, and restrict access via VPN or IPSec. This is the standard way to provide access without opening port 3389 to the world.
Good security and compliance practices
Strengthen RDP by activating NLAUsing modern encryption protocols and, if your framework requires it (GDPR/HIPAA), enabling strong cryptography policies (e.g., FIPS) and valid certificates issued by a trusted CA. Block public exposure, limit to private networks/VPNs, and enforce MFA on the gateway or the broker.
Finally, keep an eye on the logsApply patches regularly and perform periodic audits. Most RDP problems can be avoided with a combination of these measures. good policiesclear firewall rules and monitoring.
Passionate writer about the world of bytes and technology in general. I love sharing my knowledge through writing, and that's what I'll do on this blog, show you all the most interesting things about gadgets, software, hardware, tech trends, and more. My goal is to help you navigate the digital world in a simple and entertaining way.