- WDAC allows granular control over the execution of applications and code in Windows, ensuring that only authorized software can run and blocking potential threats.
- The process of generating, testing and deploying WDAC policies can be done using official tools, graphical wizards, PowerShell and online generators adapting the level of control to the needs of each organization.
- To ensure a secure and seamless deployment, it is recommended to start in audit mode, monitor the logs and make adjustments before activating mandatory enforcement mode.
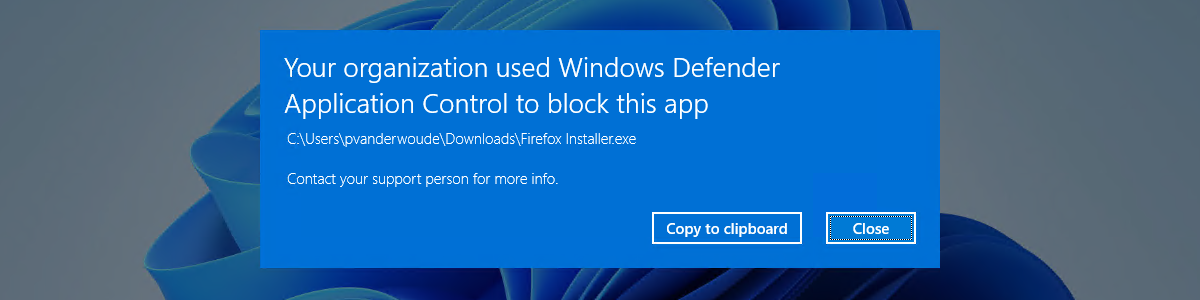
Windows Defender Application Control (WDAC) It has become a key piece to increase the security of any computer or infrastructure in modern Windows environments. More and more organizations and advanced users are looking for ways to generate WDAC policies tailored to your needs, whether to block unauthorized applications, protect critical endpoints or minimize risks from threats such as malware, malicious scripts and attacks of type living-off-the-landHowever, the process of creating and managing these policies can seem complex at first glance, so having clear and up-to-date guidance makes all the difference.
In this article, we will break down in detail all the options, recommendations, tools and practical steps to create and implement WDAC policies in any environment, from small businesses to complex enterprise environments. We'll leverage technical information from leading sources and provide tips for avoiding common problems, optimizing management, and getting the most out of this advanced Windows security feature.
What is Windows Defender Application Control (WDAC) and what is it used for?
WDAC is an advanced security solution for controlling what code can run on a Windows system.Compared to traditional antivirus or firewall-based models, WDAC takes a proactive approach: only software explicitly allowed according to configured policies is executed, eliminating the default execution of unknown binaries, malware, and unsigned scripts.
This makes it the ideal tool for protecting critical workstations, servers, and endpoints with sensitive data or highly privileged users. WDAC is more powerful than other solutions like AppLocker, as it acts at the kernel level and supports different validation methods: digital signature, hash, path, publisher name, etc. Additionally, it allows you to control not only applications, but also drivers, DLLs, modules, scripts, and extensions, ensuring that only trusted components run.
Advantages of implementing WDAC policies
There are numerous reasons to implement WDAC in your infrastructure, especially if security is a priority:
- Complete blocking of unauthorized binaries, including malware, unsigned software, or attack tools.
- Mitigation of persistent threats, such as attacks with LOLBins, scripts from insecure locations, or unauthorized lateral execution.
- Greater granular control about which files can be executed, who can do so and from where, allowing policies to be defined at different levels: basic and complementary by group or user.
- Advanced audit: WDAC can be activated in audit mode to record potentially blocked activities before activating strict enforcement mode, minimizing disruption risks.
- Integration with modern management tools such as Intune, Windows Admin Center, Group Policy, and MDM solutions, facilitating centralized administration and policy deployment.
- Enhanced protection for scripts and installers (PowerShell, MSI files, DLLs, etc.), blocking unsigned executions or executions outside the defined security standards.
WDAC usage scenarios and flexibility
WDAC is especially suitable for business environments where safety, risk management, and regulatory compliance are priorities. Some examples where WDAC makes a difference:
- User teams with high privileges or access to sensitive data
- Servers exposed to the Internet or with critical functions
- Endpoints in industrial environments, workstations, or call centers
- Teams running legacy or UWP apps that need granular control
- BYOD scenario where it is key to separate permitted applications from personal ones
Thank you to your flexible operating modesYou can start by setting WDAC to audit mode to monitor without blocking, adjust your policy based on feedback, and when you're ready, switch to enforcement mode to securely apply restrictions in production.
Components and architecture of a WDAC policy
The core of WDAC is the policy (or set of policies) you define. These policies can have various configurable elements:
- Editor or publisher rules: Allow or block applications based on the publisher of the digital signature
- Hash rules: control the execution of specific files (even if they change location)
- Rules of the road: specify folders or paths where code is allowed to run
- Package rules: useful especially for apps UWP or installed from the Store
- Rules for scripts, DLLs, and drivers: control the execution of non-direct executable components
- Exceptions and custom rules for specific coverages (for example, allowing Citrix software components with specific signatures or specific binaries in update scenarios)
In addition, WDAC supports the combination of a basic policy and several complementary ones, which allows for central control, but tailored to the specific needs of each department, group, or user. Supplementary policies can only expand the base permissions, never restrict them, so it's key to design them thoughtfully.
How to Create and Enforce WDAC Policies: Tools and Procedures
Creating WDAC policies can be approached from different angles and with various tools, depending on the degree of customization and the management environment. We summarize the main methods and recommended steps.
WDAC Policy Wizard
For those looking for automation and ease, the most accessible way is to use the Windows Defender Application Control Policy Wizard, available in Windows 10/11 and in the WDAC Policy Wizard tool from Microsoft. This utility step by step guide by defining main rules, selecting templates, including custom rules and generating policy files (.xml y .cip).
Some highlights of the process:
- Choose the "Signed and Trusted Mode" template to ensure compatibility with signed Windows components, Store components, and drivers.
- Enable first the audit mode to test the policy and analyze the impact before applying it to production
- Add custom rules (by hash, path, publisher, etc.) based on your organization's specific software
Once the rules are created, you can manually edit the file .xml for fine adjustments, and then convert it to binary format (.cip, .p7b) suitable for application by copying to the path C:\Windows\System32\CodeIntegrity\CiPolicies\Active and system reboot.
Creating Policies Using PowerShell
For advanced administrators, PowerShell is the preferred method for its flexibility and automation:
- Generate base policy:
New-CIPolicy -Level Publisher -Fallback Hash -FilePath "C:\WDAC\AuditPolicy.xml" -UserPEs -AllowFramework -AllowCatalogs - Convert policy to binary:
ConvertFrom-CIPolicy -XmlFilePath "C:\WDAC\AuditPolicy.xml" -BinaryFilePath "C:\WDAC\AuditPolicy.bin" - Implement in the system:
Copy-Item "C:\WDAC\AuditPolicy.bin" "C:\Windows\System32\CodeIntegrity\SIPolicy.p7b"
In audit mode, everything is allowed but any blocked attempts are logged, allowing you to refine the policy before activating real enforcement mode.
Using online WDAC policy generators
For those looking for speed and do not want to install tools, there are services such as WDAC Policy Generator that allow you to create files .xml y .cip personalized through online formsSimply choose your Windows version, audit mode, route rules, hash, editor, upload reference files, and download the generated policy ready to be applied.
Best practices and specific recommendations
It is recommended to follow some good practices to ensure a correct deployment:
- Always initialize in audit mode to prevent accidental crashes of critical or business software. Monitor logs (
Event Viewer > Microsoft-Windows-CodeIntegrity/Operational, event 3033) before tightening policy. - Update the rules after each deployment, especially after installing or updating relevant software (Citrix applications, drivers, own tools).
- Includes specific rules for vendor binaries that do not update their files frequently or that distribute unsigned executables (for example, third-party binaries on older Citrix VDAs).
- Use small base policies combined with specific complementary policies to scale permissions based on groups, departments, or temporary needs.
- In environments where management software such as Windows Admin Center, it is essential to add the necessary certificates and rules to avoid blocking administrative or connectivity functions (Microsoft Code Signing PCA 2011 certificates, rules for WiX, etc.).
- Control SMB access In remote administration, ensuring that the necessary ports (445 TCP) are open and UNC permissions are correctly managed.
Troubleshooting common problems and limitations
When applying WDAC policies, some errors may appear. frequent problems:
- Blocking legitimate binaries after a partial software update (e.g., Citrix VDA update that does not update third-party binaries).
- “Module not found” errors or connection failures in Windows Admin Center due to missing necessary permissions or rules.
- Policy desynchronization between base and supplemental policies, causing some applications to be blocked even though they should be allowed.
To address them, it is useful to:
- Review logs and events in Event Viewer after policy changes.
- Reapply and adjust rules after installing new software or updates.
- Revert to audit mode in case of incidents, review the policy, and reapply the correct rules.
Advanced management: special cases and control of specific applications
WDAC can manage UWP apps, extensions, modules, scripts, and controllers, even on devices like HoloLens. For UWP apps, it's essential to know your PackageFamilyName, obtained through PowerShell or Device Portal, to define specific protection or blocking rules.
You can also define custom rules to block specific versions of browsers such as Microsoft Edge, using detailed rules that specify the file name and version:
<Deny FriendlyName="C:\Data\Programs FileRule" PackageVersion="65535.65535.65535.65535" FileName="msedge.exe" />In environments with multiple roles or remote administration using tools like Intune or MDM, it's critical to coordinate policy updates across all nodes to maintain consistency and security.
How to verify the implementation of WDAC policies and monitor their impact
To ensure your WDAC policies are working properly, review the events in the Events viewer in the route Application and Services Logs → Microsoft → Windows → CodeIntegrity → Operational. 3033 events indicate that the policy has been triggered, and blocking or audit entries show the actions taken.
You can also use PowerShell to filter for crash-related events:
Get-WinEvent -LogName "Microsoft-Windows-CodeIntegrity/Operational" | Where-Object { $_.Message -like "*would have been blocked*" }
It's important to validate that blocked files are threats or unauthorized components, and adjust the policy if false positives are detected that could affect normal operations.
Implement and maintain custom WDAC policies It is an efficient strategy to increase security, reduce exposure to threats, and ensure that only authorized software runs on your infrastructure, although it requires dedicated planning and continuous tuning.
Passionate writer about the world of bytes and technology in general. I love sharing my knowledge through writing, and that's what I'll do on this blog, show you all the most interesting things about gadgets, software, hardware, tech trends, and more. My goal is to help you navigate the digital world in a simple and entertaining way.