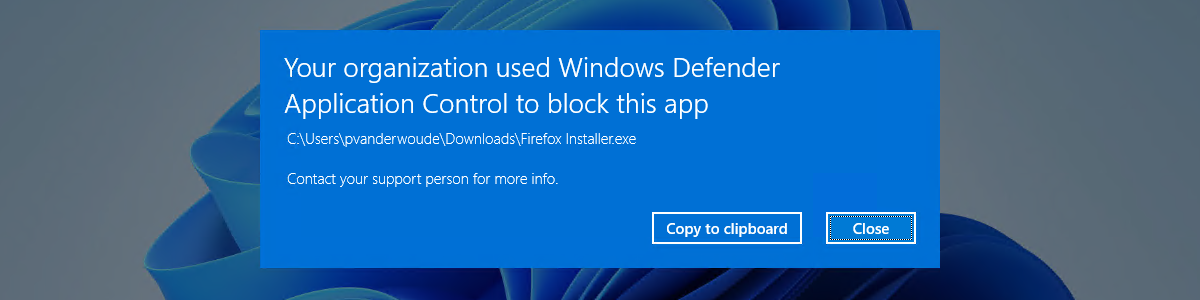
- AppLocker allows you to fine-tune the execution of applications in Windows 11.
- Audit mode and pre-testing are key to avoiding accidental crashes and maintaining productivity.
- Integration with group policies and third-party tools facilitates centralized and scalable management.

Have you ever wondered how protect your computer or your company's computer against the installation and execution of unwanted applications in Windows 11? AppLocker is one of those powerful tools that many have heard about, but not everyone knows how to fully utilize. If you want to take full control of what runs on your system, here you will discover how to do it step by step, clearly, with Tricks and recommendations so that you don't miss anything.
In this practical guide we are going to break down everything necessary to Configure AppLocker from scratch to a robust implementation in both home and business environments. Plus, you'll learn how to properly create, test, and deploy policies so you don't get caught in the middle or have problems with vital applications accidentally crashing.
What is AppLocker and what is it used for in Windows 11?
AppLocker is an advanced feature of app control Available in the professional and business editions of Windows. Its purpose is very clear: to allow you to make decisions with all the details which executables, scripts, installers and other software components are authorized to run on your computers. This capability is especially useful in organizations where software security and standardization are a priority, but also for individual users who want to protect their environment.
With AppLocker it is possible to create specific rules for different groups of users or computers, based on attributes such as the application publisher, name, path, or even the hash of the file. This allows you to establish policies to allow or deny the execution of specific applications, file types, or versions, all in a centralized and automatable manner.
Why use AppLocker on Windows 11?
The main reason to use AppLocker is raise the level of security in any Windows environment. By limiting which applications can run, you dramatically reduce the risks of malware, unauthorized software, or even users installing programs that could compromise stability or regulatory compliance.
AppLocker offers advantages such as:
- Total flexibility: You can define very precise rules.
- Easy integration with group policy in corporate environments.
- Audit mode for testing without affecting users.
- Automation and management from console or through PowerShell.
Prerequisites and considerations before starting
Before you jump into setting up AppLocker, there are a few things you should keep in mind to avoid problems and work efficiently:
- Compatible Windows EditionAppLocker is available on Windows 11 Pro, Enterprise, and Education. If you have a Home edition, you unfortunately won't be able to use it natively.
- Administrator permission: You need administrative rights to both create and apply policies.
- Understanding file types and rules: AppLocker allows you to control executables (EXE), installers (MSI), scripts (BAT, PS1, etc.), libraries (DLL), and Store applications (APPX).
- Establish an implementation plan: very relevant in companies; it is advisable to document what you want to achieve and how it will be implemented.
- Using audit mode: essential to verify that rules do not block what they should not before moving to production.
- Identity Application Service (appidsvc): Required to be enabled and set to start automatically.
Getting Started: Planning and Designing AppLocker Policies
To ensure that setting up AppLocker in Windows 11 is a success and not a headache, it is recommended to follow a logical sequence:
- Define your goals: Do you want to restrict only unlicensed software? Protect critical applications? Prevent users from installing apps non-corporate?
- Take inventory of applications: Identifies the software used in each user group or department.
- Decide what types of rules you need: by publisher, path, hash, product name, etc. Each option has its advantages depending on the use case.
- Organize your policies by groups: Leverage your Active Directory structure or Windows security groups to apply policies granularly.
TrickIn businesses, document policies well and keep them up to date to avoid unexpected blockages when updates or changes are made to authorized software.
Creating Policies: Collections and Rule Types
AppLocker manages its rules by grouping them into collections depending on the file type. Each collection can have its own compliance mode (audit or enforcement). The available collections are:
- Executables (EXE)
- Installers (MSI and MSP)
- Scripts (e.g., BAT, CMD, JS, PS1)
- DLL Libraries
- Microsoft Store Apps (APPX)
The rules within each collection can be defined by:
- Editor (digital signature): very useful to allow or block all software signed by a specific company.
- File path: to allow or deny applications based on your location.
- File hash: Identifies the application by its unique fingerprint.
Detailed steps to create and configure AppLocker policies
1. Access the administration tool
For individual devices, you can use secpol.msc (Local Security Policy). In corporate environments, it is ideal to work from the Group Policy Management Console (GPMC)From here you can create, edit, and import AppLocker policies for both a single computer and an entire domain.
2. Creating policies and generating rules
The usual process is:
- Open the corresponding tool (secpol.msc or GPMC).
- Navigate to Security Settings -> Application Control -> AppLocker.
- Select the rule collection you want to configure.
- You can create rules manually or use the Rule Generation Wizard, which will help you automate the creation of rules based on files already present in the system.
When creating a rule, you choose whether it applies to all users, a specific group, or an individual user. Rules also allow for exceptions, providing even more flexibility.
3. Compliance mode: enforce or audit
For each collection you can choose between these modes:
- Apply rules: The policy is active and blocks/allows as defined.
- Audit only: The rules do not block anything, but events are logged for later analysis.
- Not configured: The collection is not managed by AppLocker.
Council: Always starts in audit mode. This way, you can identify potential unwanted blockages without affecting productivity.
4. Import and export of policies
AppLocker allows you to export policies to XML files for backup, transfer, or deployment to other computers. This way, you can develop and test a policy in an isolated environment and then seamlessly transfer it to the live environment.
Testing and validating AppLocker rules
1. Turn on audit mode
Before activating app blocking, verify that the policy is working as expected. Audit mode allows you to record all events that would trigger a crash without actually blocking anything.
2. Enable and configure the Application Identity service
Without the service appidsvc AppLocker isn't applicable. Go to Windows Services and make sure it's set to automatic and running on all target computers.
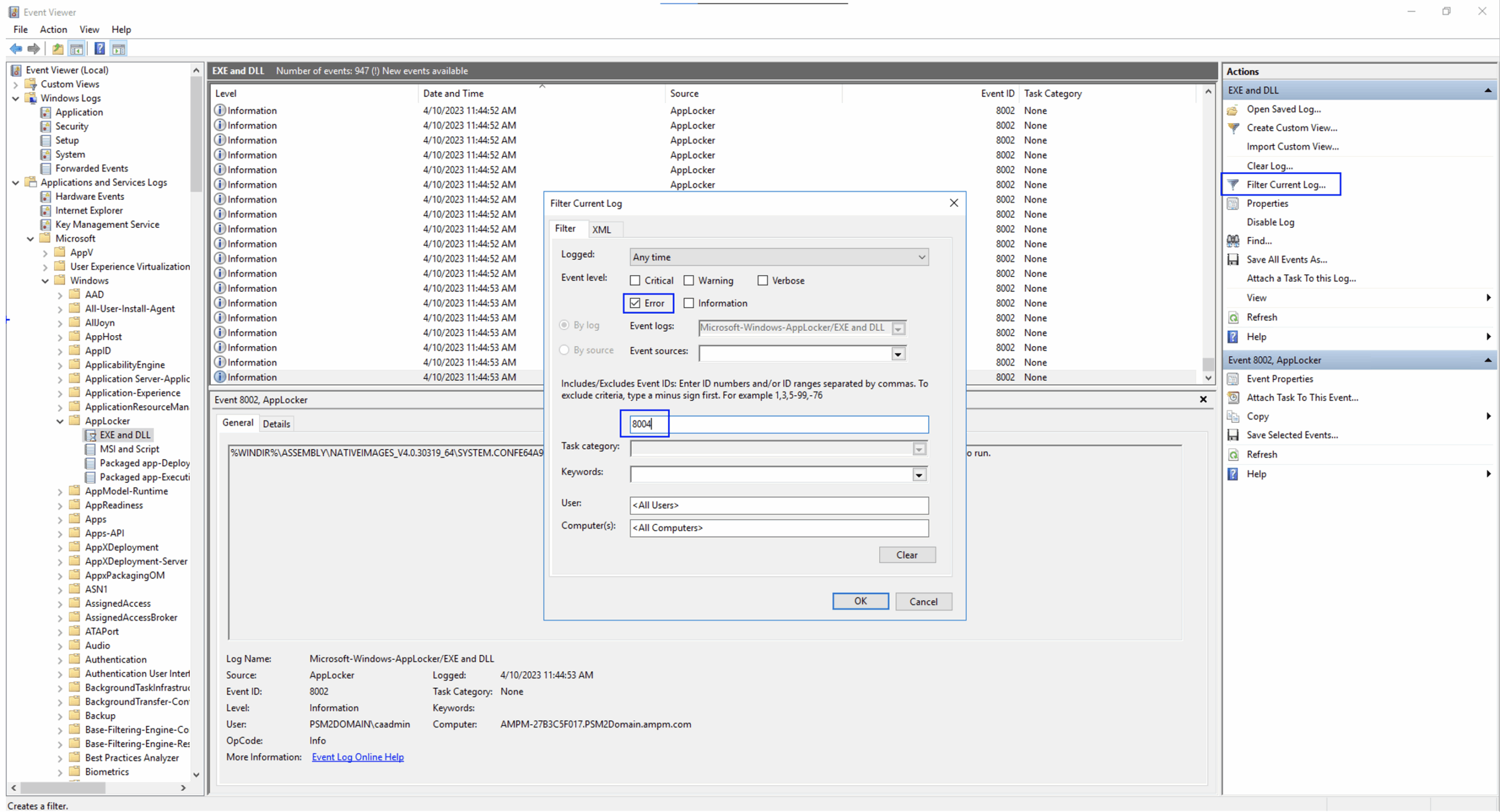
3. Use analysis tools
You can manually review the Event Viewer looking for AppLocker logs, or use the PowerShell cmdlets on the table:
- Get-AppLockerFileInformation: To get details of files related to AppLocker events.
- Test-AppLockerPolicy: to check if a policy would affect a specific file.
If you detect that a legitimate application would be blocked, you have the opportunity to adjust the rule before the policy actually goes into effect.
4. Iterative modification and retesting
It's common for necessary applications to appear blocked during initial tests. Adjust the rules, repeat the tests, and don't switch to application mode until everything is working as expected.
Deployment and implementation of the directives
Once the configuration is ready and verified, it's time to deploy it to the live environment. You can do this in two ways:
- Locally: Using the Local Security Policy on each individual computer.
- Through GPO- Ideal for enterprise environments where you need to manage dozens or hundreds of computers. Simply link the GPO to the required organizational unit, and the policy will be applied automatically.
Remember that any subsequent policy changes can be exported/imported to maintain consistency across computers. If you want to maintain version control, you can use tools like Advanced Group Policy Management.
AppLocker Monitoring, Auditing, and Maintenance
Once your policies are in place, you can't forget about them. Regular monitoring is crucial to:
- Monitor logs AppLocker for blocked execution attempts.
- Review technical support requests, in case a legitimate user cannot run a necessary application.
- Update policies in response to changes in the software catalog or company needs.
Windows Event Viewer and the logs Correspondents are your allies here. You can filter by AppLocker events and analyze blocking patterns. Additionally, using event subscriptions or PowerShell scripts, you can centralize capture and analysis across multiple computers.
How to Block and Allow Specific Apps: Advanced Example Using XML and Google Workspace
It is also possible to manage AppLocker in environments where Windows is managed from third-party solutions, such as Google Workspace. In these cases, application restriction is performed uploading custom XML files generated in PowerShell or from the graphical Group Policy editor.
The process, in broad terms, would be:
- Create the policy XML file with the appropriate rules for file types (EXE, MSI, Script, DLL, APPX).
- Define in the XML attributes such as type, policy name, SID of the user or group to which it applies, action (allow/block), publisher, file name, version, etc.
- Upload the configuration from the administration console (e.g., Google), choosing the appropriate OMA-URI depending on the file type you want to block or allow.
- Assign the custom setting to the desired organizational unit or device group.
A key aspect is to properly manage SIDs for users and groups, ensuring that the policy impacts only those it should. Remember that you can use wildcards in certain fields to cover more applications without writing a rule for each one.
If you're looking to allow only signed apps or block specific apps, the XML framework allows for this by combining rules that both authorize trusted executables and specifically block executables you know shouldn't be used (e.g., older versions of an app, or programs that are no longer licensed).
Safety considerations and good practices
- Using AppLocker significantly increases protection, but it's not foolproof. It's always advisable to complement it with other measures, such as antivirus, log monitoring, and regular updates.
- A bad configuration can block essential applications, so it is crucial to audit mode and perform extensive testing before implementing it in production.
- To avoid issues with updates, take advantage of version and digital signature options in publisher-based rules. This way, you don't need to update the policy every time a patch or new release of the permitted software is released.
- Document the entire process, changes, and exceptions for future maintenance or internal audits.
Frequently Asked Questions about AppLocker in Windows 11
- Is AppLocker free? Yes, it is included in the Professional and Business editions of Windows at no additional cost.
- Can it be used on Windows 11 Home? No, it is missing in the Home version.
- What happens if I accidentally block an essential program? Use audit mode during testing and monitor blocking events. If this happens in production, you should modify the rule as soon as possible to unblock the affected application.
- How many types of rules can I combine? As many as you need, mixing conditions by editor, path and hash.
- Can you avoid sophisticated malware? It greatly reduces risk, but it doesn't replace other layers like anti-malware or user education.
Managing AppLocker in Windows 11 may seem daunting at first, but properly configured, it's a true shield against threats and software installation disruptions. By following these steps and tips, you'll be able to Configure AppLocker step by step in Windows 11 Effectively. Don't forget to periodically review the rules and update them as the application catalog you use evolves, and always rely on audit mode and pre-testing to avoid unpleasant surprises.
Passionate writer about the world of bytes and technology in general. I love sharing my knowledge through writing, and that's what I'll do on this blog, show you all the most interesting things about gadgets, software, hardware, tech trends, and more. My goal is to help you navigate the digital world in a simple and entertaining way.